Privacy Settings
This site uses third-party website tracking technologies to provide and continually improve our services, and to display advertisements according to users' interests. I agree and may revoke or change my consent at any time with effect for the future.
Deny
Accept All
Platform
Platform Overview
Platform Features
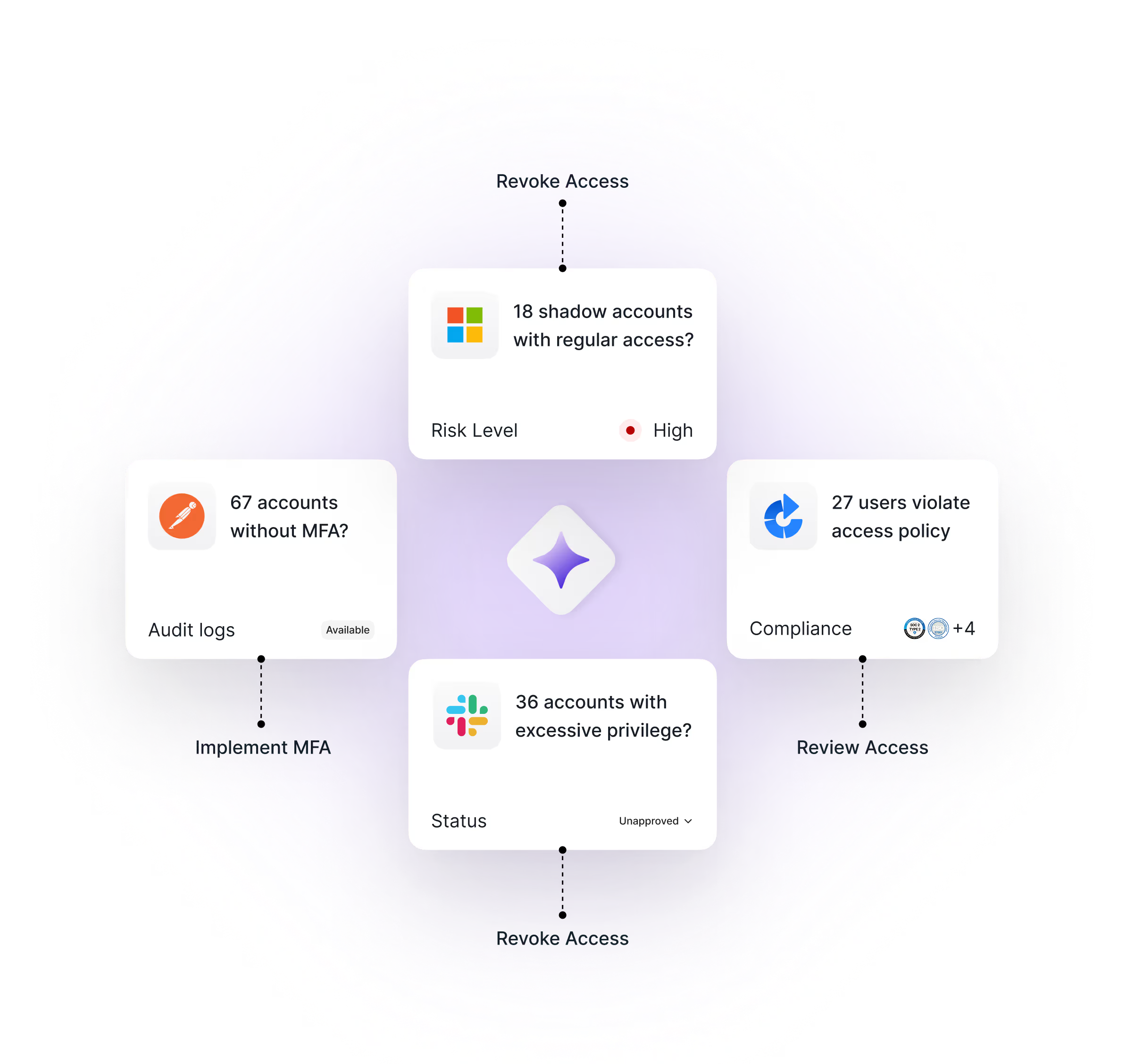
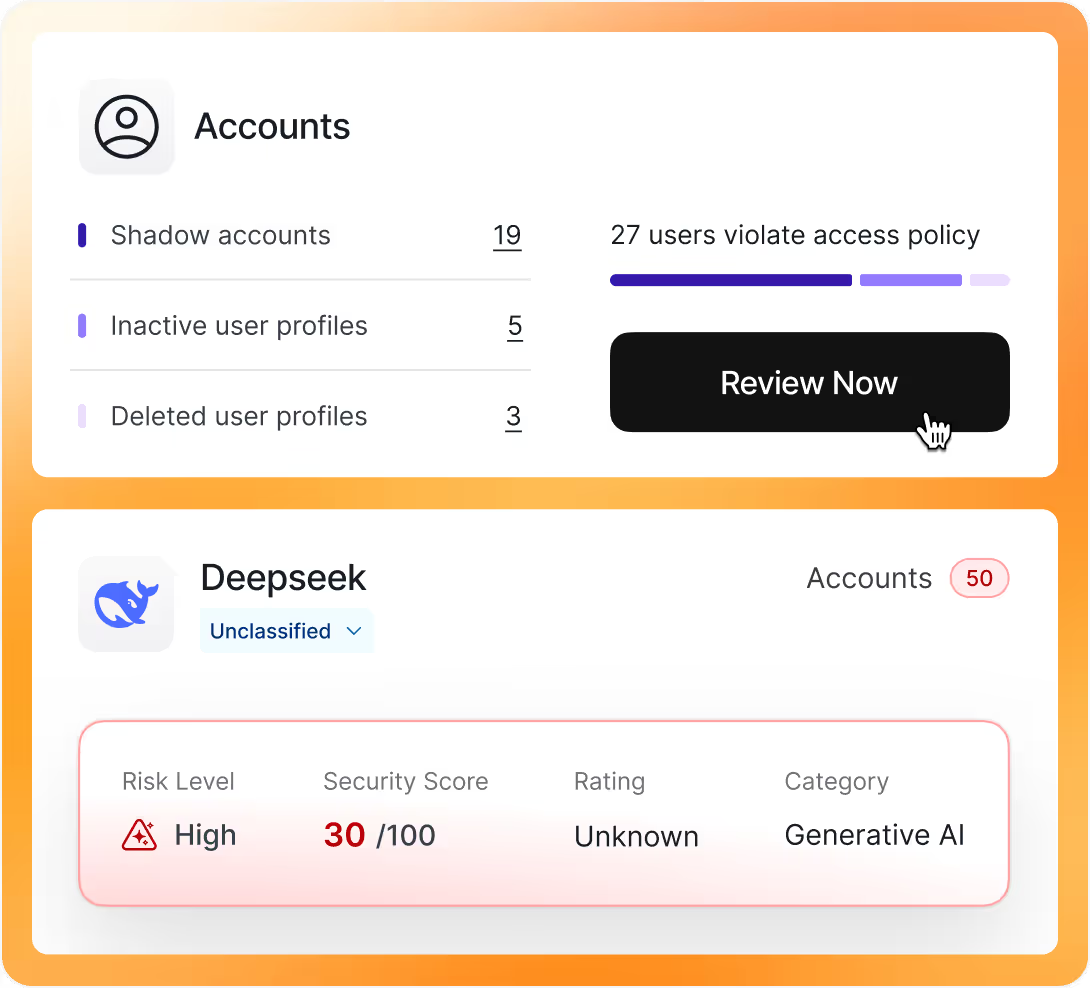
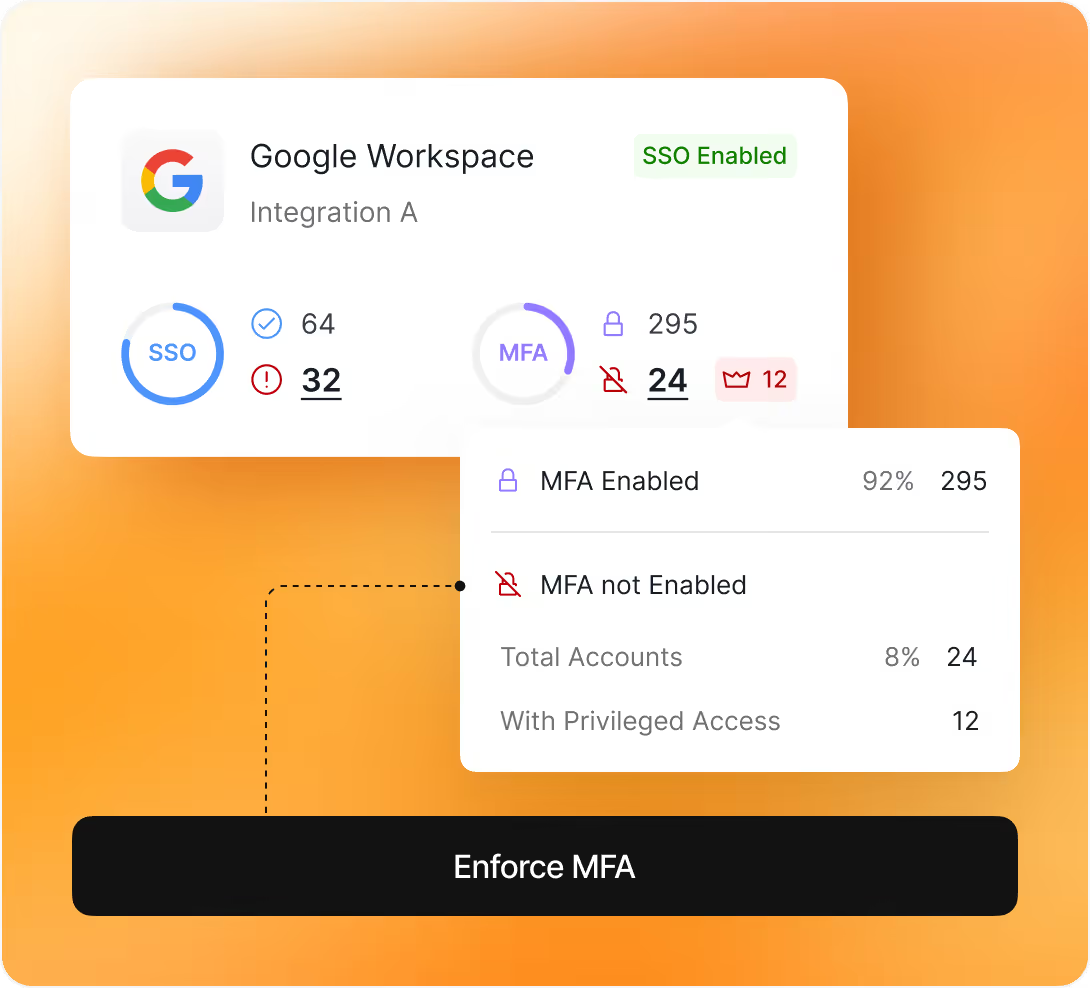
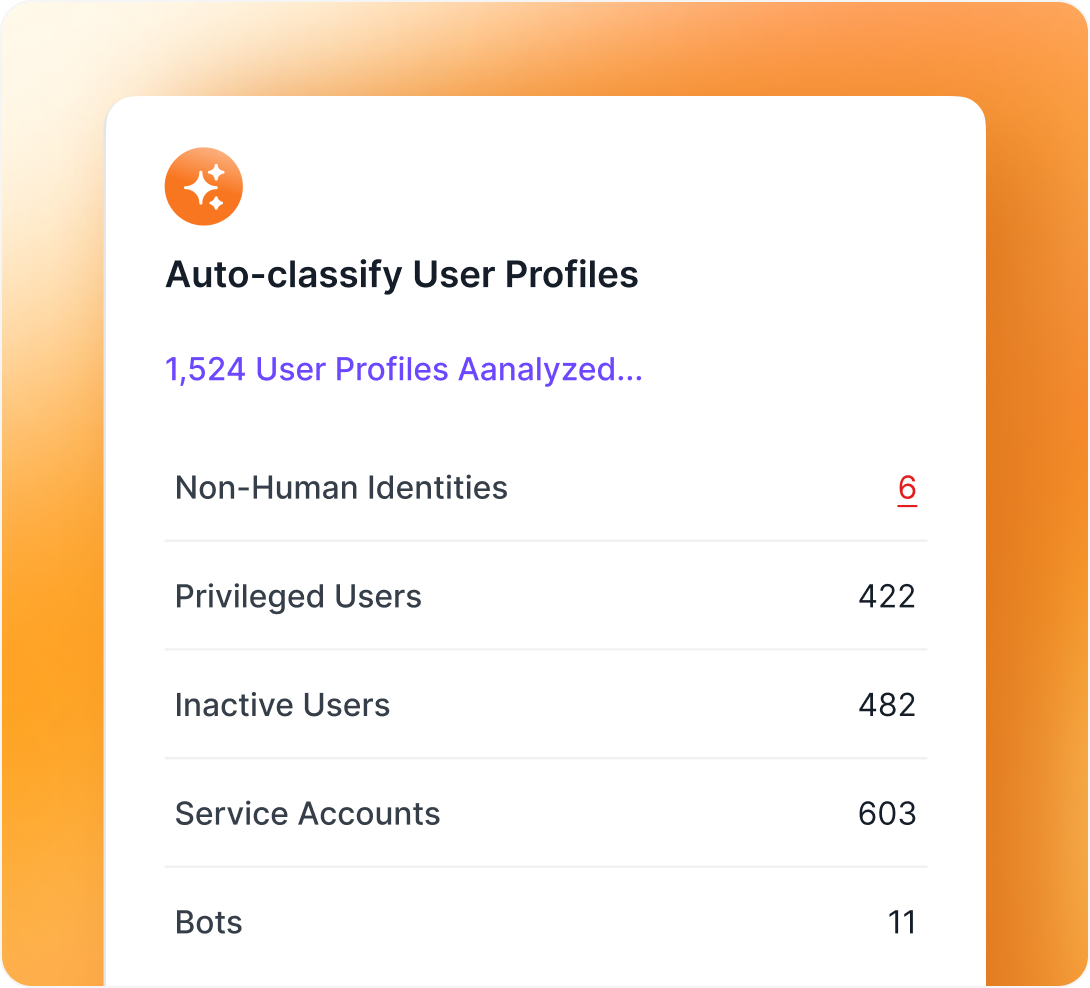
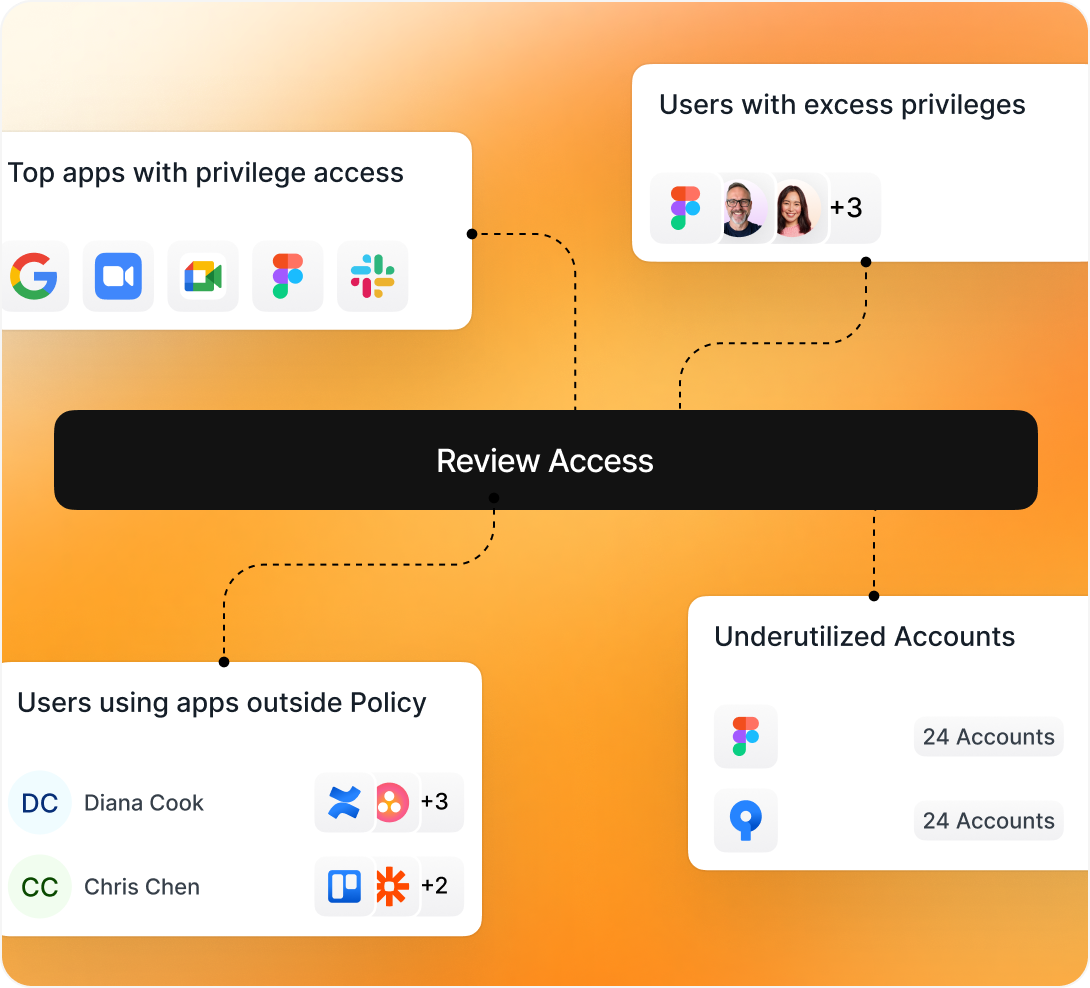
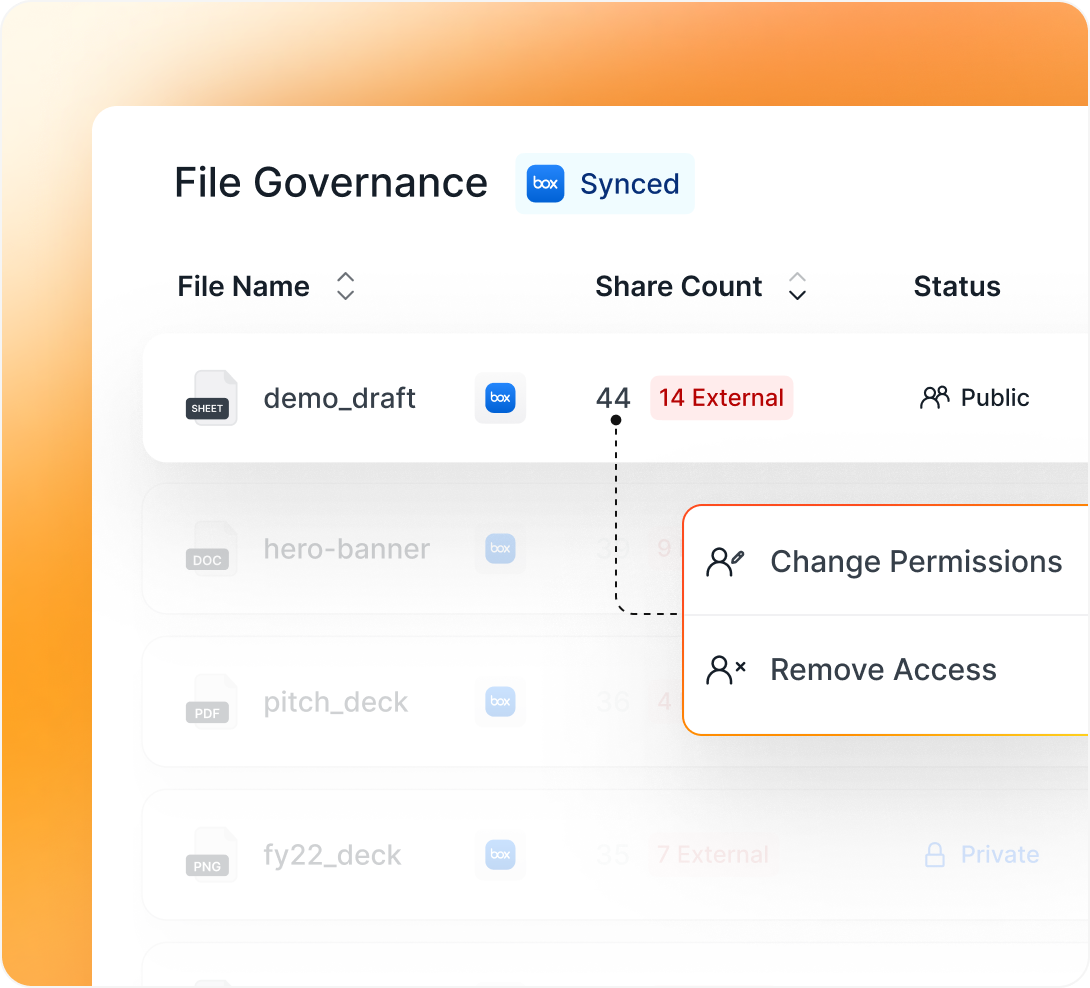
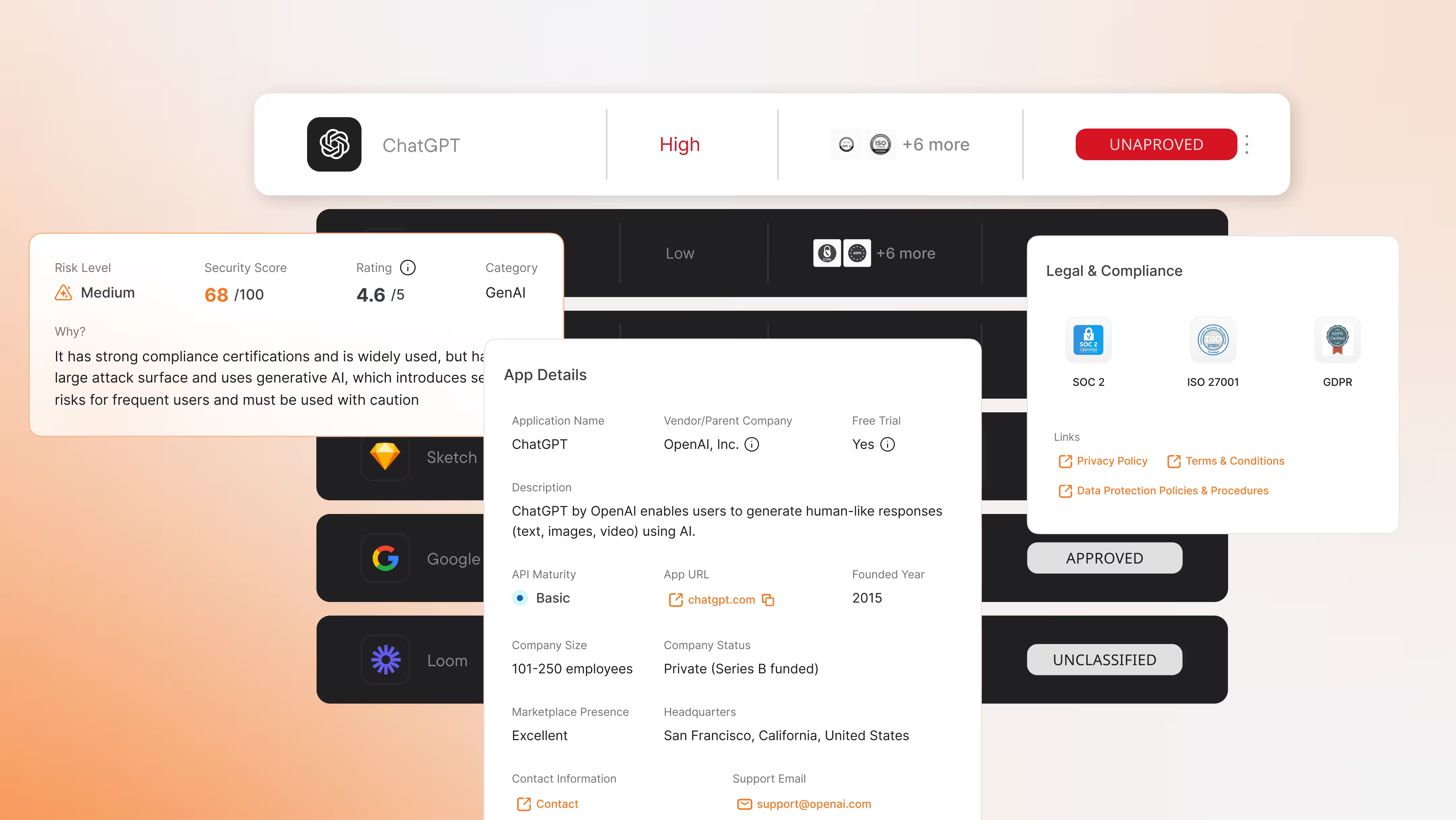
More than 350 app integrations for deeper insights and better control.
See IntegrationsSolutions
Menu
Close
Privacy Settings
This site uses third-party website tracking technologies to provide and continually improve our services, and to display advertisements according to users' interests. I agree and may revoke or change my consent at any time with effect for the future.
Deny
Accept All