What Is Privileged Access Management?
Join hundreds of companies and start your SaaS management journey today

Privileged Access Management (PAM) is a cybersecurity strategy and set of technologies designed to control, monitor, and secure access to an organization's most critical systems and sensitive data. It focuses specifically on managing and protecting "privileged accounts," those with elevated permissions that can make significant system changes, access confidential information, or control critical infrastructure.
As Darren Guccione, CEO and Co-founder of Keeper Security, states, “[organizations'] risk of data breaches and cyberattacks increases exponentially if they have not deployed a PAM solution.” Guccione further emphasizes that a majority of “successful breaches involve stolen or compromised credentials,” meaning that organizations of all sizes need a PAM solution that proactively stays one step ahead.
A robust PAM solution provides several critical capabilities:
- Access control: Limiting privileged access to only those who absolutely need it
- Session monitoring: Monitoring and analyzing privileged sessions
- Just-in-time access: Granting temporary privileges only when needed
- Least privilege enforcement: Ensuring users have only the minimum permissions necessary
Why PAM Solutions Are Important?
PAM solutions prevent unauthorized access to privileged accounts while enabling legitimate users to perform their duties securely. These privileged accounts are prime targets for cyberattacks because they provide access to:
- Administrative systems and databases
- Financial records and intellectual property
- Network infrastructure and security controls
- Cloud environments and production servers
But why does it matter?
- Prevent Data Breaches: 80%+ of security breaches involve compromised privileged credentials
- Meet Compliance Requirements: Regulations like SOC 2, HIPAA, and PCI-DSS mandate privileged access controls.
- Reduce Insider Threats: Monitoring prevents both malicious and accidental misuse
- Support Zero Trust Security: Verifies every access attempt regardless of user status
For example, DevOps teams use Privileged Access Management (PAM) to secure elevated permissions in AWS. All credentials are stored in HashiCorp Vault and accessed through SSO and MFA.
When engineers need admin access, they request it (JIT) just-in-time and receive temporary credentials that expire after 60 minutes. PAM proxies record all privileged sessions for auditing in Splunk, while Jenkins pipelines retrieve short-lived IAM tokens from Vault at runtime, eliminating the need for static credentials.
This approach enforces least privilege, removes standing admin rights, ensures full auditability, limits credential exposure, and supports compliance with SOC 2, ISO 27001, and PCI-DSS standards.
Key Components of Privileged Access Management
PAM involves several key components that work together to secure privileged accounts throughout their lifecycle.
Credential Vaulting & Rotation
- Stores privileged credentials in encrypted vaults
- Eliminates shared passwords and hard-coded credentials
Access Control & Session Management
- Just-in-time (JIT) access that grants permissions only when needed
- Session recording and monitoring for audit trails
- Multi-factor authentication (MFA) for privileged accounts
Privilege Elevation & Delegation
- Allows temporary elevation of user privileges for specific tasks
- Enforces least-privilege principles by limiting permissions to the minimum necessary
- Automated workflows for approval and access requests
How the Josys Platform Tackles Privileged Access Management
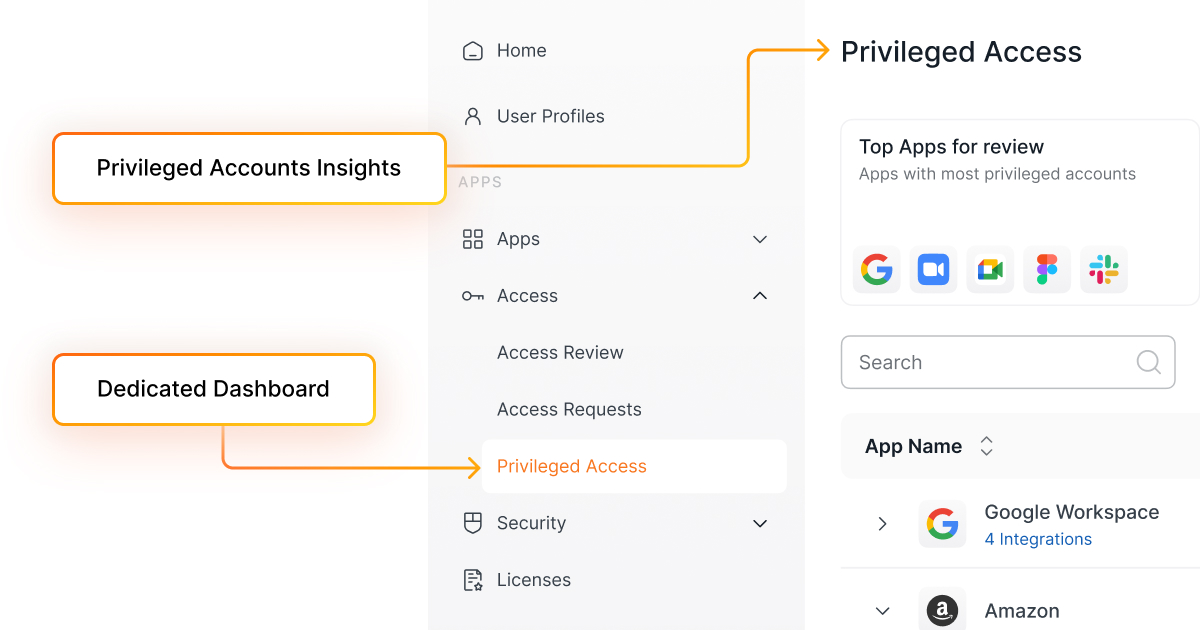
At Josys, we've built our platform with privileged access management at its core. Our approach focuses on making sophisticated security accessible and manageable for organizations of all sizes.
"Privileged access management isn't just about security—it's about enabling business growth while protecting your most valuable assets," says Tim Silva, Product Design Lead at Josys. "We've designed our PAM capabilities to be both powerful and intuitive, ensuring that organizations can implement robust security without adding complexity. In today's threat landscape, this balance of security and usability isn't just nice to have; it's essential for survival."
The Josys platform provides:
- Comprehensive visibility: A unified dashboard showing all privileged accounts, their owners, and their access levels
- Automated lifecycle management: Streamlined provisioning and deprovisioning of access rights as employees join, move within, or leave the organization
- Just-in-time access: Temporary elevation of privileges with automatic expiration
- Detailed audit trails: Complete records of who accessed what and when
- Seamless integration: Connection with your existing identity management and security tools
Beyond Security to Business Enablement
Privileged access management is no longer just a security best practice; it's a necessity. As organizations increasingly rely on digital systems and face growing regulatory requirements, the ability to control, monitor, and audit privileged access becomes critical.
Effective PAM does more than prevent breaches; it enables digital transformation by giving organizations the confidence to adopt new technologies without increasing risk. It supports compliance efforts by providing the evidence auditors require. And it improves operational efficiency by streamlining access processes that would otherwise consume valuable IT resources.
By implementing a comprehensive privileged access management strategy with Josys, organizations can transform a potential security liability into a business advantage—protecting their most valuable assets while enabling the agility they need to thrive in today's digital economy. Interested in learning more? Book a demo to learn more.
over your SaaS?
Sign-up for a free Josys account to transform your IT operations.


















